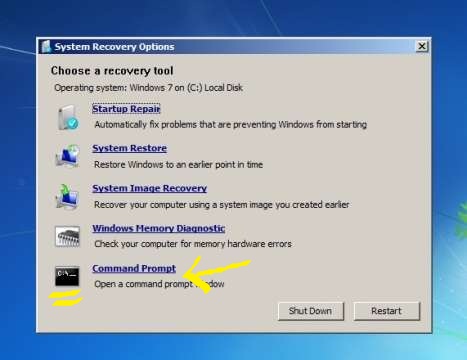
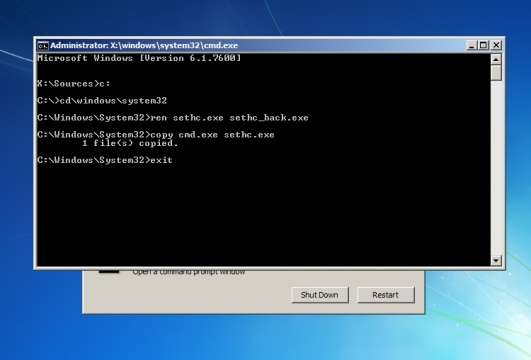
These days, schools are so strapped for cash, they cant afford the Internet bandwidth for students to do useful and fun thing on school computers. Some schools expect students to actually do work during IT lessons, and some IT departments just don’t like YouTube. However, the days are over when they can lock down the system enough to stop determined students from using the Internet as they please.
De-filters
These are websites which take a URL, and collect the content for you. The work because the filters only see you downloading data from an unblocked website (the de-filter); the connection to the banned site is from another external web server so it doesn’t pass through your schools filters.
These are some good de-filter websites:
These are just a few of the hundreds of de-filter websites revealed by a quick google search. Where possible, tick the box that turns on some kind of encryption. This prevents the IT department seeing what sites you gave unblocked. Also, sites that use the HTTPS protocol are even harder to be caught with.

However, de-filter sites do not always unblock active content such as flash, or videos so they are not perfect. If you find a good de-filter, don’t give it to anyone because it will soon spread round the school, and end up blocked.
Using a new proxy
Most school filters work by directing all traffic through a proxy server, which scans URLs for blocked keywords. Internet Explorer uses the system wide proxy for HTTP. However, FireFox can have its own proxy set. Firefox will route all traffic through the open proxy server, avoiding using banned keywords in the URL. This traffic will then be sent through the filter proxy by the operating system, but will not be blocked if all has worked well.
1) Get a copy of FireFox on a memory stick. It’s best to use the portable version available here because it wont leave evidence of running FireFox on the main system hard drive. This version also remembers your bookmarks, passwords etc.
2) Set up FireFox to a proxy. Open the Tools menu, then click Options. Then click the Connection Settings button in the resultant window. Click the radio button for “Manual proxy configuration”, and fill in relevant proxies/port numbers. A list of free proxies and port numbers is available here. Now, all should work as planned.
HTTPS
This is the most simple of them all but sometimes does not to work. It’s as simple as just adding an S on to the http. so lets say for example http://www.facebook.com/ you would change it to https://www.facebook.com/
![]()
UltraSurf
In my high school we use a program called UltraSurf. http://www.ultrareach.com/ All you need to do is download this to a flash drive (some kids save it to our student drives on our network, but I don’t suggest this as the IT department will find out) and when you are at school run it. It will pop up with a new browser window and viola! Surf the net as you please!
URL Filter Bypassing
It’s possible for internal employees to bypass Web-content filtering applications and logging mechanisms to browse to sites that they shouldn’t go to — potentially covering up malicious behavior and Internet usage.
Easier hack is to exploit the general mechanism built into URL filtering systems that filter Web traffic based on specific URLs and keywords (words that match a list or meet a certain criteria). Users take advantage of this practice by converting the URL to an IP address and then to its binary equivalent. The following steps can bypass URL filtering in such browsers as Netscape and Mozilla:
- Obtain the IP address for the Web site.
For example, a gambling Web site (www.go-gamblin.com) blocked in Web-content filtering software has this IP address: 10.22.33.44 This is an invalid public address, but it’s okay for this example; you may want to filter out Web addresses on your internal network as well.
- Convert each individual number in the IP address to an eight-digit binary number. Numbers that may have fewer than eight digits in their binary form must be padded with leading zeroes to fill in the missing digits.
For example, the binary number 1 is padded to 00000001 by adding seven zeroes. The four individual numbers in the IP address in Step 1 have these equivalent eight-digit binary numbers:
10 = 00001010
22 = 00010110
33 = 00100001
44 = 00101100
The Windows Calculator can automatically convert numbers from decimal to binary notation:
i. Choose View➪Scientific.
ii. Click the Dec option button.
iii. Enter the number in decimal value.
iv. Click the Bin option button to show the number in binary format.
- Assemble the four 8-digit binary numbers into one 32-digit binary number. For example, the complete 32-digit binary equivalent for 10.22.33.44 is 00001010000101100010000100101100 Don’t add the binary numbers. Just organize them in the same order as the original IP address without the separating periods.
- Convert the 32-digit binary number to a decimal number. For example, the 32-digit binary number 00001010000101100010000100101100 equals the decimal number 169222444. The decimal number doesn’t need to be padded to a specific length
- Plug the decimal number into the Web browser’s address field, like this: http://169222444
- The Web page loads easy as pie! The preceding steps won’t bypass URLs in Internet Explorer.